Phishing scam lures Office 365 users with phony voicemail
In recent weeks, a new phishing campaign targeting Office 365 users has emerged. The scam uses fraudulent voicemail messages to lure users into giving up their email credentials.
Researchers at McAfee found that several major companies have been targeted by the scam. Targeted industries include service, financial, retail, education and healthcare institutions.
According to McAfee reports, a user receives an email notifying them of a missed phone call and includes a request to login to their account to access the associated voicemail.
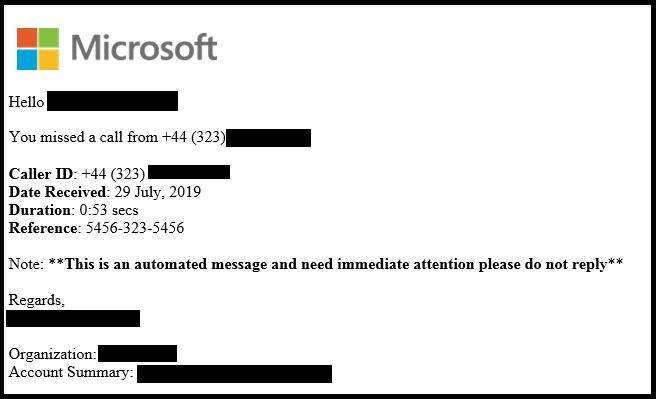
Source: McAfee.com
The email also contains an attached HTML file. When loaded, the file redirects the user to the phishing website. While there are multiple versions of the attachment, most contain an audio recording of someone talking to convince the user that the voicemail is legitimate.
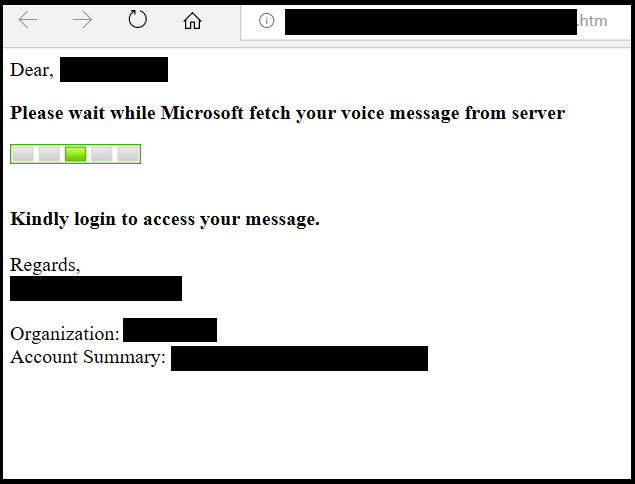
Source: McAfee.com
McAfee notes the following file names used for the HTML attachments in this phishing email.
- 10-August-2019.wav.html [Format: DD-Month-YYYY.wav.html]
- 14-August-2019.html [Format: DD-Month-YYYY.html]
- Voice-17-July2019wav.htm [Format: Voice- DD-MonthYYYYwav.htm]
- Audio_Telephone_Message15-August-2019.wav.html [Format: Audio_Telephone_MessageDD-Month-YYYY.wav.html]
Once redirected to the phishing website, the user is presented with a phishing page where they are prompted to enter their login credentials. On this page, not only does it look identical to the official Office 365 login page, but also, the user’s email address is shown on the page, further leading them to believe that the fraudulent site is real.
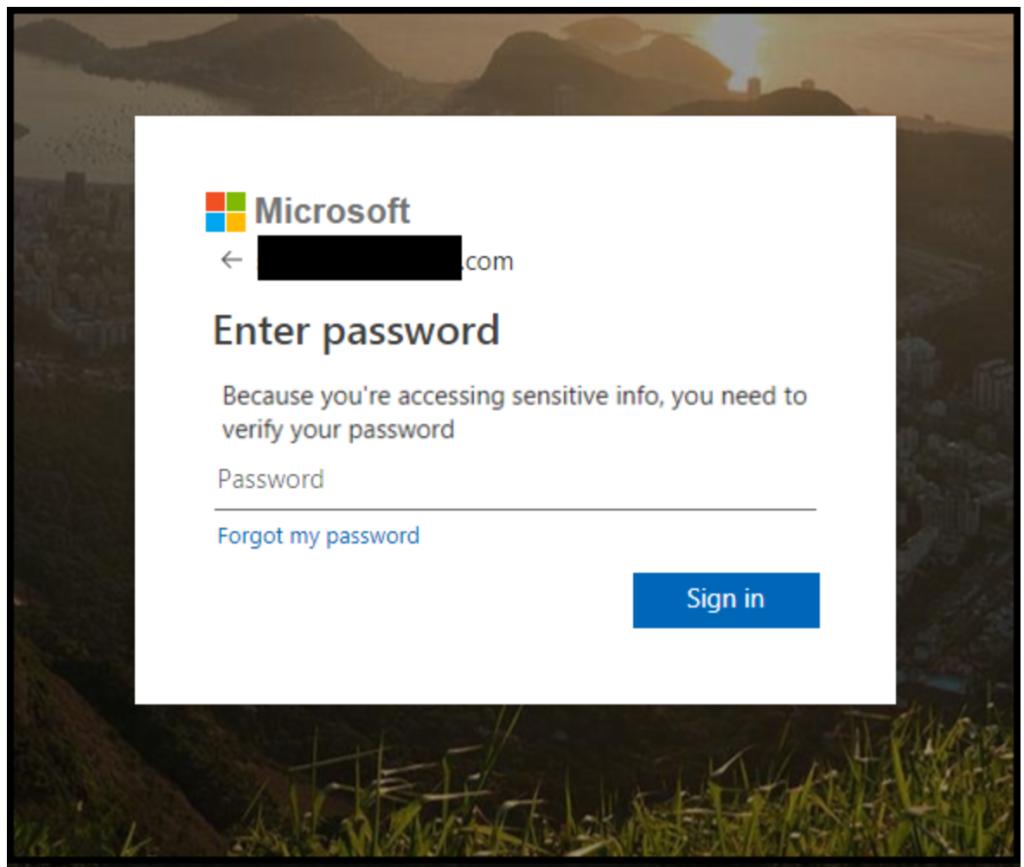
Source: McAfee.com
After entering their password, the user is shown a successful login page, then redirected to the Office.com login page.
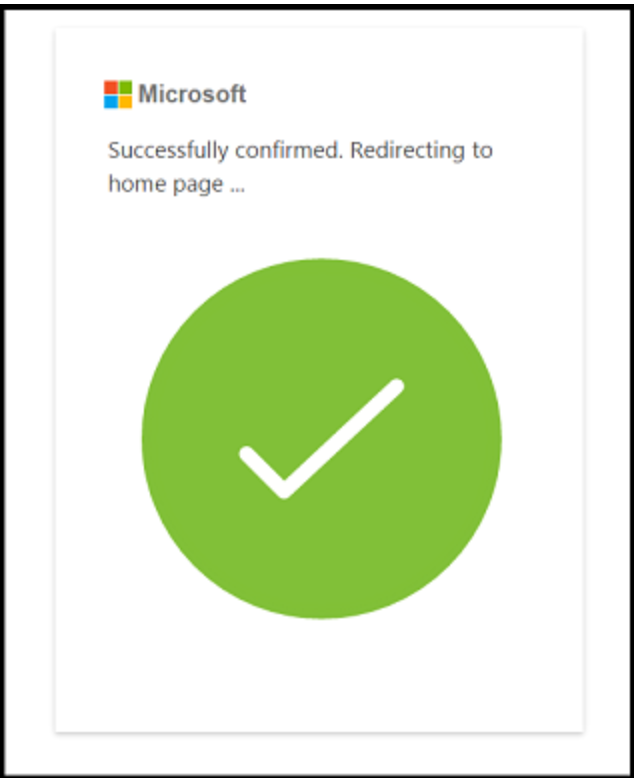
Source: McAfee.com
Protect Yourself, Protect Elon
When it comes to protecting your data and university data, it’s critical to be aware of the signs. When you are presented with a login page for a Microsoft account, please note that these pages should only appear on microsoft.com, live.com, microsoftonline.com and outlook.com domains only. If you are presented with a Microsoft login form from any other URL, such as the example shown above, DO NOT enter your login credentials and report this potential threat to Elon’s information security team at infosec@elon.edu.
Visit McAfee to learn more about this phishing scam and visit Elon’s Information Security website to explore additional red flags commonly found in phishing emails and more ways to protect yourself, your data and your devices.
Source: McAfee
 Follow
Follow