Phishing email scams target Microsoft Office 365, OneNote users
These days, it comes as no surprise that scammers are constantly thinking up new ways to take advantage of internet users.
BleepingComputer recently highlighted two phishing email scams targeting Microsoft users. These emails lure users in by appearing to be legit and alerting them to urgent security concerns. Ultimately, scammers are trying to get users to provide login credentials. Learn more about these scams below, and how to protect yourself and Elon from the danger they pose.
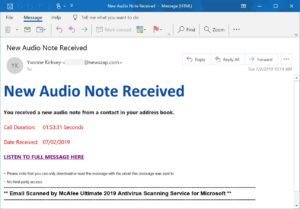
The Scam: OneNote Audio Note Phishing Campaign
First a phishing email with the subject “New Audio Note Received” and claims that the user has received a new audio message from a contact in their address book, and that they must click on a link in the email to hear the message, according to BleepingComputer.
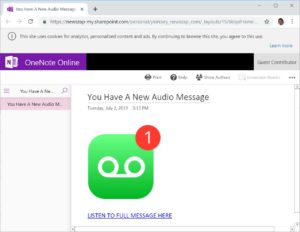
When the user clicks “Listen to full message here” in the email, they are taken to a fake OneNote webpage hosted on Sharepoint.com. The page prompts them to clink another link to hear their new audio message.
When the user clicks the fraudulent link to hear the message, they are taken to a fake Microsoft 365 sign-in page. Once a user submits their login credentials on the fake sign-in page, their data, and potentially university data, has been compromised.
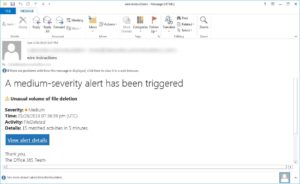
The Scam: Office 365 File Deletion Alert Phishing Campaign
This phishing scam starts with an email that pretends to be from the “Office 365 Team.” The email goes on to warn the recipient that an unusual amount of file deletions is occurring on their account, triggering a medium-severity alert, according to BleepingComputer. It also instructs the user to review the alerts.
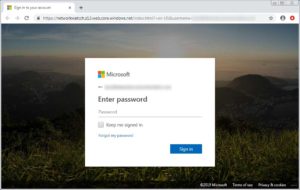
When the user clicks the fraudulent link in the phishing email, they are taken to a fake Microsoft 365 sign-in page, as featured below. Once a user submits their login credentials on the fake sign-in page, their data, and potentially university data, has been compromised.
Protect Yourself, Protect Elon
When it comes to protecting your data and university data, it’s critical to be aware of the signs. When you are presented with a login page for a Microsoft account, please note that these pages should only appear on microsoft.com, live.com, microsoftonline.com and outlook.com domains only. If you are presented with a Microsoft login form from any other URL, such as the example shown above, DO NOT enter your login credentials and report this potential threat to Elon’s information security team at infosec@elon.edu.
Learn more about these scams at BleepingComputer.com, and visit Elon’s Information Security website to explore additional red flags commonly found in phishing emails and more ways to protect yourself, your data and your devices.
Source: BleepingComputer.com
 Follow
Follow