Two-step verification: something you know and something you have
Guest post by Jeff Stern, a student in Professor Lynn Heinrichs’ information security class.
 If a hacker were to log into my email account, they could get data about my financial information, confidential research information and private conversations. For this reason, I have activated two-step verification to protect my account with extra security and encourage you to do the same. Considering the amount of sensitive data we share on the web, it may no longer be enough to rely on a simple alphanumeric password. Two-step verification, also known as two-factor authentication, is a relatively simple way to further secure your online accounts. The driving idea behind two-step verification is that to log into your account you not only need to enter a secret password but also data from a device that you have (eg. a randomly-generated code from your cell phone) or a biometric (eg. a fingerprint, retina scan). The former is currently the most popular, although with advancing technologies the latter category could become commonplace before we know it.
If a hacker were to log into my email account, they could get data about my financial information, confidential research information and private conversations. For this reason, I have activated two-step verification to protect my account with extra security and encourage you to do the same. Considering the amount of sensitive data we share on the web, it may no longer be enough to rely on a simple alphanumeric password. Two-step verification, also known as two-factor authentication, is a relatively simple way to further secure your online accounts. The driving idea behind two-step verification is that to log into your account you not only need to enter a secret password but also data from a device that you have (eg. a randomly-generated code from your cell phone) or a biometric (eg. a fingerprint, retina scan). The former is currently the most popular, although with advancing technologies the latter category could become commonplace before we know it.
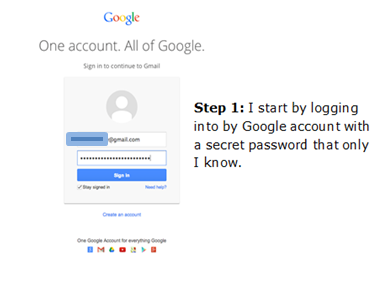
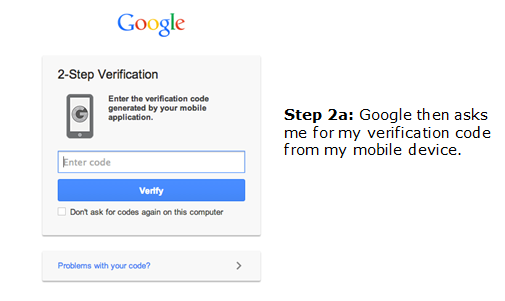
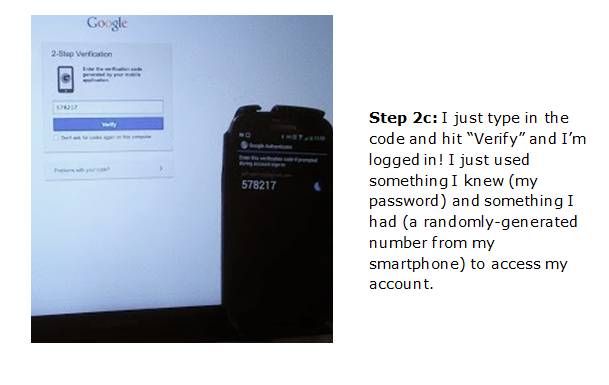
If you activate two-step verification on your Google account, it becomes nearly impossible for a hacker to log into your account unless they also steal your cell phone. To demonstrate two-step verification, here’s how I log into my Google account…
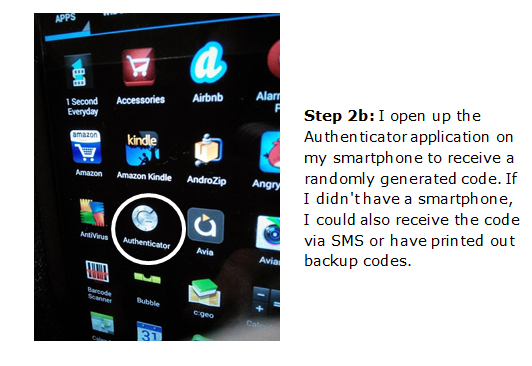
As you can see, this does require some extra work on my part when I’m logging into new computers but only you can disable the need to use the Authenticator code on personal devices like your laptop.
Generally tech writers and security experts agree that two-step verification will decrease potential data breaches. If you still have concerns, Matt Cutts debunks many common myths about two-step verification. I encourage you to give it a try for yourself as the extra effort required is certainly worth the peace of mind.
Visit Google’s documentation for more information about two-step verification.
 Follow
Follow